A company's personal or business-related data requires special protection. Guaranteeing the security of this data and thereby also protecting our customers, business partners and employees is a top priority for TRUMPF. That is why we have established appropriate organizational and technical measures for data protection, information security and IT security.

Data security
Our customers, business partners and employees can trust us to handle information of all kinds responsibly.
How do we handle data protection at TRUMPF?
Today, the protection of personal data is of the utmost importance. We meet this requirement with our data protection management system.
We take comprehensive precautions to ensure the confidentiality, integrity and availability of information - and actively protect ourselves and our products from cyber attacks.
Do you have a question about data protection or do you want to provide confidential information to us? Contact us - in person or anonymously.
How we protect data
TRUMPF has implemented a data protection management system (DSMS). This ensures the protection of personal data through various measures, structures and processes. Thus we avoid legal violations in connection with the processing of personal data. Our data protection management system consists of six modules that build on each other.
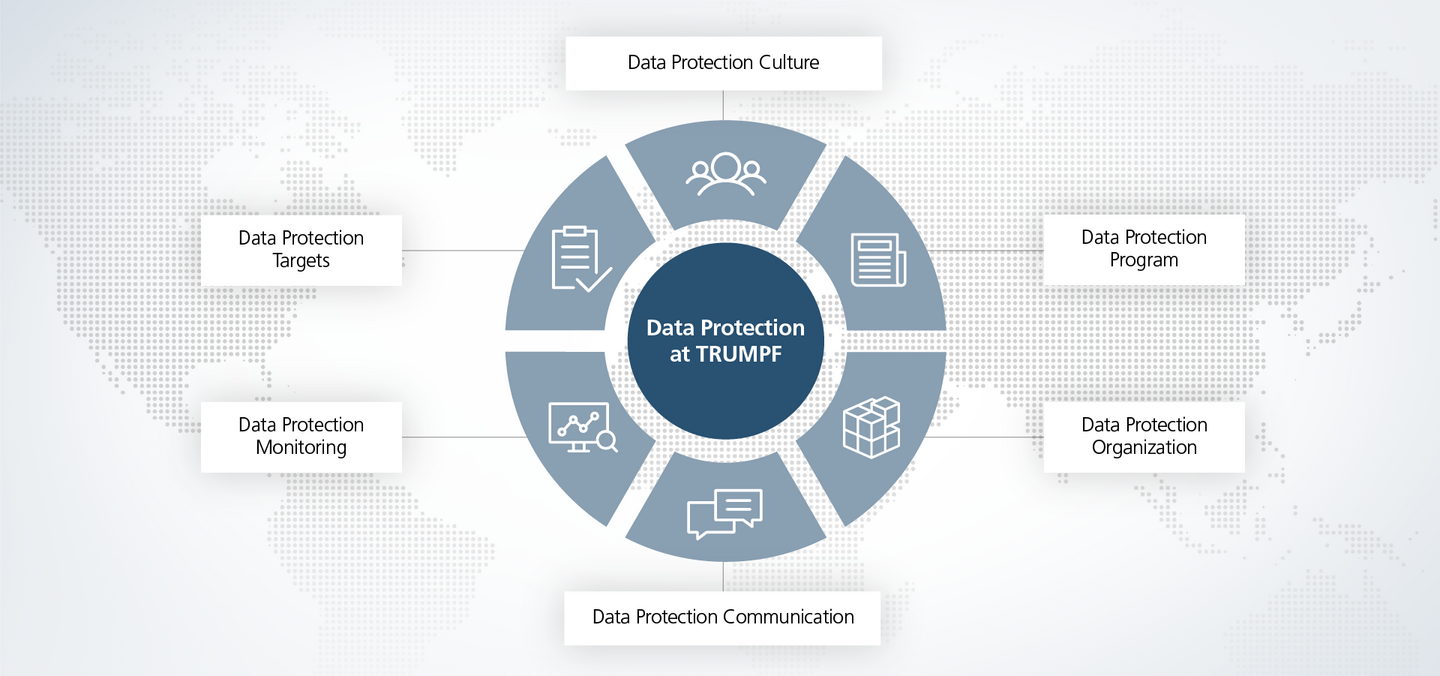
Our data protection culture is an integral part of the compliance culture and is embedded in the TRUMPF Code of Conduct. With a high level of diligence, we train our employees to conscientiously handle data of all kinds.
Our data protection program ensures the implementation of and compliance with data protection at TRUMPF. The program defines the principles and basic measures to prevent and stop data protection violations. The essence of the program is formed by the TRUMPF data protection guideline.
Our data protection organization consists of around 60 contacts. They ensure that all employees are familiar with the data protection management system. At the same time, they are available as contact persons for our employees and for public inquiries.
Data protection communication not only actively raises awareness, but also ensures active listening, so that data protection risks are identified and avoided at an early stage. This includes, for example, the provision of e-learning courses or classroom training for managers and employees.
With the help of data protection monitoring, we collect and evaluate all data relevant to data protection. The central data protection team in Ditzingen then uses the results to derive measures to improve the data protection management system.
For each fiscal year, the central data protection team, in coordination with the group data protection officer, defines objectives for increasing the effectiveness of the data protection management system. Once a year, the central data protection team compares the objectives with the results and establishes new objectives.
Our data protection organization
How do we respond to data protection risks or prevent them from occurring in the first place? These are two topics that the Group Data Protection Officer deals with along with the data protection team in Ditzingen and the data protection network. This is how we ensure the transfer of the data protection management system into all business divisions and subsidiaries, communicate regularly with the local officers and help develop solutions.
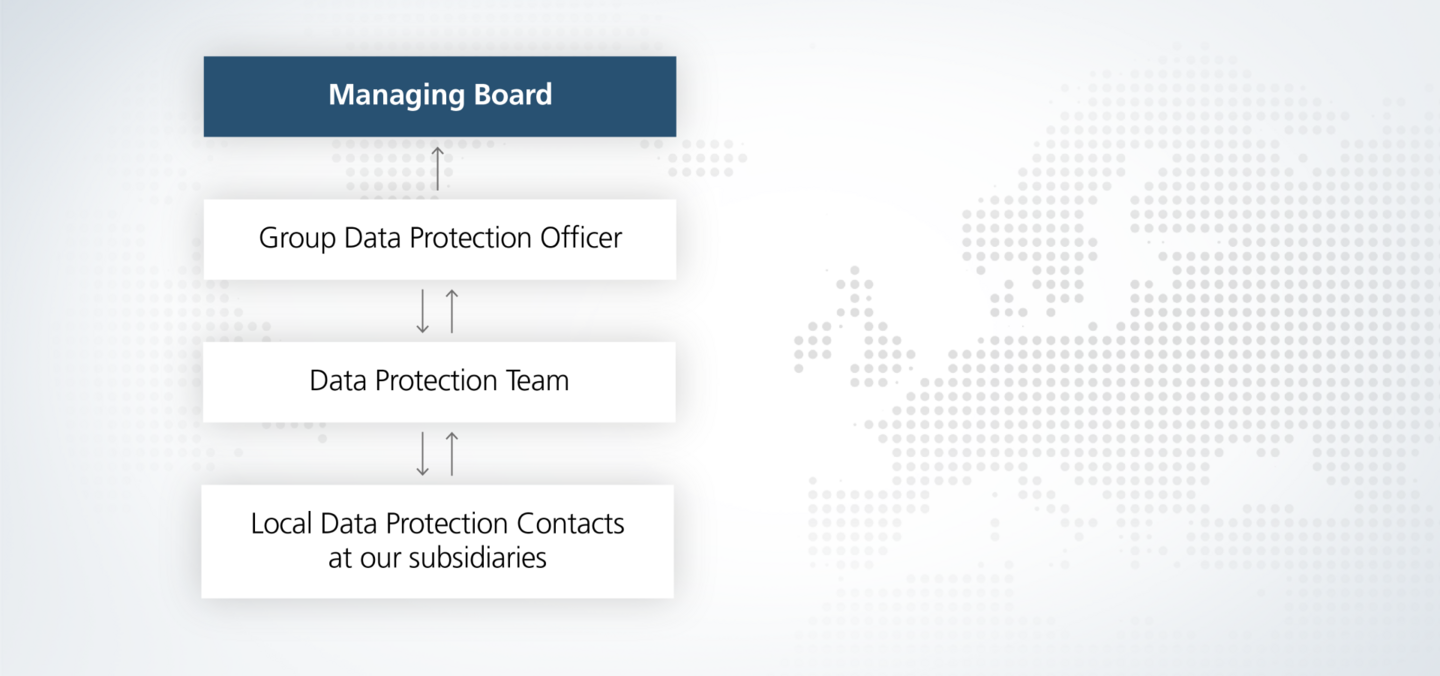
The Managing Board assumes overall responsibility for data protection in the TRUMPF Group and creates a corporate culture in which data protection regulations are observed.
At TRUMPF, the legally defined tasks for compliance with data protection regulations are carried out by the group data protection officer. Together with the central data protection team in Ditzingen, the data protection officer monitors compliance with data protection laws and our data protection guidelines. The data protection officer is responsible for processing data protection complaints and communicating with the data protection supervisory authorities. Communication and training measures are also implemented by the data protection officer. They also advise responsible parties and specialist departments on all data protection issues.
The central data protection team in Ditzingen is part of the central department Corporate Law, Integrity &Risk and supports the group data protection officer as a staff unit in all data protection-related cases.
In order to manage data protection issues, we also rely on local contact persons in the subsidiaries and central departments who work on site. They support the respective management team in the implementation of data protection requirements.
Our data protection monitoring
With data protection monitoring, we collect measurable data and performance indicators from data protection activities at TRUMPF. We have established a reporting process in the event of a breach of personal data protection. This guarantees a quick response to data breaches and violations and ensures that the protection of personal data is restored as quickly as possible.
In addition, the central data protection team carries out audits at the subsidiaries in order to regularly check the level of data protection there.
How we ensure information and IT security at TRUMPF
With our IT and information security, we want to prevent damage to TRUMPF, our business partners, customers and employees. We implement appropriate organizational and technical measures for this purpose. We use these measures to protect information of all kinds as well as our technical systems and products from cyber attacks and the resulting failures. We have already initiated an ISO27001 certification process.
We follow clear principles, such as need-to-know, least privilege or security by design. We consistently implement these principles through guidelines and processes.
Our information security management system (ISMS) is derived from international standards such as the ISO 27001 standard. We also regularly review and update our regulations and processes. Among others, we specifically explore the following topics:
-
Secure software development and product security: Security when using TRUMPF products and services is our top priority. Therefore, strict guidelines apply to our software development. In order to protect our customers' machines and systems, we identify security vulnerabilities, inform our customers about them and provide them with the necessary security updates. All current information and updates can be found here at a glance.
-
Clear requirements for suppliers: Our suppliers must meet our IT and information security requirements. We secure this contractually, with non-disclosure agreements among other measures. This is how we ensure that external products and services comply with our security guidelines.
-
Network security, data security and recovery processes: We continuously monitor all networks and manage access in a targeted manner.
-
Protection against malware: We use extensive measures to detect malware and protect our company against it. Among other things, we have regulated our employees' handling of all storage media.
-
Access to systems: We protect all of our information systems from unauthorized access through high security standards and approval processes. We set high standards for passwords and authentication.
-
Security incidents: We investigate (potential) security incidents and handle them accordingly to avoid possible security risks.
Our employees are aware of their responsibility in handling information and IT systems. They are supported by a well-organized network of over 80 information security coordinators who provide them with rules and guidelines. We also ensure compliant behavior with independent audits.
We regularly hold comprehensive training courses on IT and information security, for example on secure software development.

